Flip a couple of switches in your AWS console, right? Wrong! It is so much cooler than that!
In exercise 5.3 of the AWS CSA Associate exam, there is an exercise which really wants you to stretch your wings. That is what I love about this book; getting the most out of this book requires you to use resources outside this book.
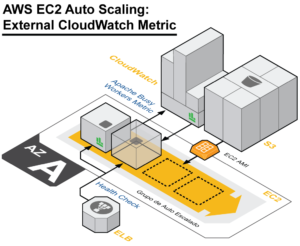
The goal of the exercise is to import custom metric sources from your EC2 instance that are not available from the CloudWatch console. What is interesting is that I only have a few instances across my AWS ecosystem, but I already have a choice of 200 metrics to dig around in, mostly from the EC2 namespace. My first thought runs to the kinds of tool sets that you will need to be running to make sense of all the data in your average Enterprise AWS environment…
First things first: Second things come later, if ever.
- You need to install a few Perl libraries: libwww-perl and libdatetime-perl. Yep, the AWS guys opted to use Perl to bridge the gap between your virtual boxes and their hypervisor. Cool.
- Download the scripts package from Amazon here:https://aws-cloudwatch.s3.amazonaws.com/downloads/CloudWatchMonitoringScripts-1.2.2.zip
- Grab your keys from a user whose role is either admin or has the appropriate cloudwatch:put/get/listmetrics permissions. The EC2:DescribeTags permission might be nice too. Take those keys and insert them into the awscreds.template file and then change the extension from template to conf.
- Boom! You’re ready to go. I fired up this agent by using the ./mon-put-instance-data.pl -mem-used-incl-cache-buff -mem-util -mem-used -mem-avail command, and it gives me all the memory usage data points that I could ever want. At this point, you will find them in the metrics section of your CloudWatch console.
- A best practice would be to set a cron job for a much more frequent update by editing the crontab file and setting in this:*/5 * * * * ~/aws-scripts-mon/mon-put-instance-data.pl –mem-used-incl-cache-buff –mem-util –disk-space-util –disk-path=/ –from-cron
Most of this is documented very thoroughly on the AWS Docs site here, but it will lack the motivational empowering rhetoric and sound effect footnotes.
https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/mon-scripts.html